How to use SAML for Single Page Applications and Mobile Apps?

Long story short, if you want to use SAML for SPAs or mobile applications, without the need for a backend server, it is not possible. Don't leave yet! There are ways to work around this limitation. In this blog post, we will explore how to use SAML for a public application like an SPA or a mobile app and provide best practices for securing your application.
SAML Limitations for public applications
SAML is a protocol that requires a trust relationship between the Identity Provider (IdP) and the Service Provider (SP). This trust relationship is established through signing and encryption keys that are shared between the IdP and the SP. The SP uses these keys to verify the authenticity of the SAML response and to decrypt the assertions contained in the response.
In a traditional web application, the SP is responsible for validating the SAML response and decrypting the assertions. This is typically done on the server side, where the SP has access to the necessary keys and can securely validate the response. But in a public application like an SPA or a mobile app, the SP cannot securely store the keys needed to validate the SAML response. This makes it difficult to implement SAML in these types of applications.
Workarounds for using SAML in public applications
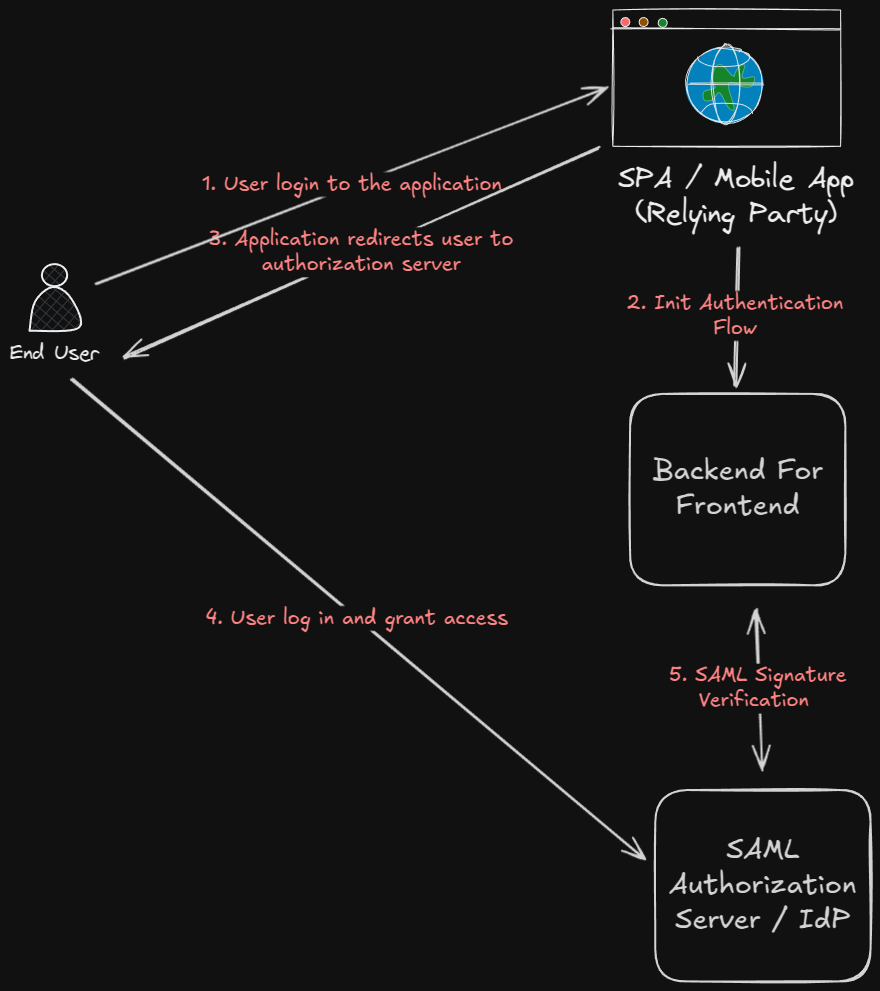
Use a backend server
One way to work around this limitation is to use a backend server to handle the SAML authentication flow. The backend server can securely store the keys needed to validate the SAML response and can handle the decryption and validation of the response. The SPA or mobile app can then communicate with the backend server to authenticate the user and retrieve the necessary information. You can see this as a proxy with session management or a component implementing backend for frontend pattern including authentication and authorization.
Stop using SAML and use OAuth2/OpenID Connect
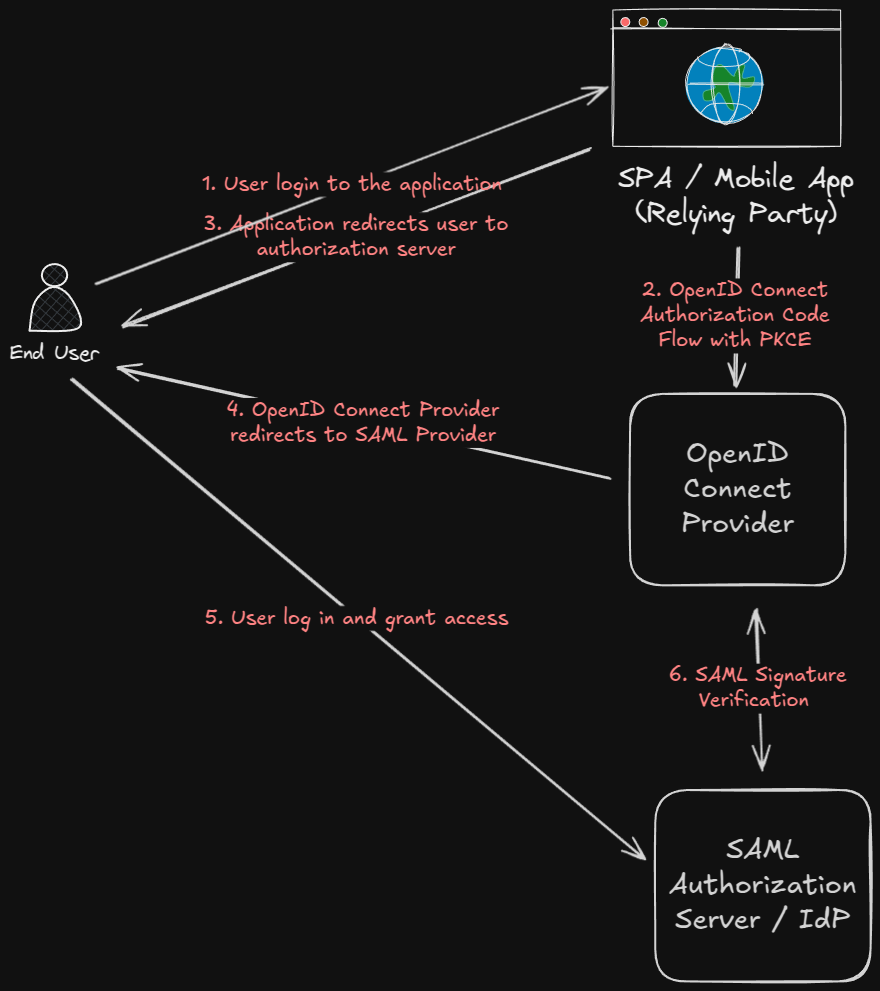
Another option is to stop using SAML and switch to OAuth2/OpenID Connect. The thing is, SAML is quite old now and has been designed when the web was different. Public application like SPA and mobile apps did not exist at that time. OAuth2/OpenID Connect is more modern and is designed to work with these types of applications. It provides a better user experience and is easier to implement in public applications.
To do so, you can use OpenID Connect Authorization Code Flow with PKCE. This flow is designed for public applications and provides a secure way to authenticate users without the need for a backend server.
If you absolutely need to use SAML, you can use OAuth2/OpenID Connect as a bridge between your public application and the SAML IdP. The public application can authenticate the user using OAuth2/OpenID Connect and then use the OAuth2 token to request a SAML assertion from the IdP. This assertion can then be used to authenticate the user with the SP.